zANTI could be named a hacking application that brings the power of Backtrack on your Android device. Once you login into zANTI, it maps your complete community and sniffs the websites being visited together with their cookies — because of ARP cache poisoning on devices.
In the same way once the hacker fails then you may be refunded instantly with none deduction. Why we do not share or take any traceable payment or specifics?
We're the most beneficial in phone monitoring. Our hackers can hack into your partner's phone, social media account and e-mails to track their pursuits. Can I Recuperate shed Bitcoins?
payment upfront from you in advance of we assign the hacker although not hand it over to your hacker. Instead we retain it on maintain with us till you
Editorial Notice: We receive a Fee from companion hyperlinks on Forbes Advisor. Commissions do not affect our editors' viewpoints or evaluations. Company cell phone options are a significant consideration for almost any group.
But that’s come to be tougher as phone manufacturers such as Apple and Google have robust security to dam malware from Main running systems, Ziring claimed.
That’s it. At a time of prevalent electronic insecurity it turns out that the oldest and most basic Laptop fix There may be — turning a device off then back again on once more — can thwart hackers from thieving information from smartphones.
This hacker-most loved tool steals cookies from your WiFi network and offers the attacker unauthorized entry to the victim’s account. Nonetheless, we advise using it only for ethical functions and proceeding only after having authorization from your goal device proprietor.
Take note: Offer repos like apt can have older versions of such applications. They may operate, but I made use of the ones within the developer web site.
However, if teams during the security functions Centre are depending on classic endpoint security tools, this regular activity isn’t staying tracked continually and properly, if it’s tracked in the least.
The 3rd-party doctrine says that when a person shares details or data with a company or maybe Yet another man or woman, she relinquishes any acceptable expectation that her information and facts will stay private.
Company Unrestricted Performance: Starts at $35 every month, compensated for every line with 5 or even more traces. It contains all the things in Starter, plus Innovative mobile security and substantial-definition streams; Just about every line has usage of 30 GB of hotspot data.
If you'd like to find out more about how one can secure your organization’s mobile devices, you'll want to have a look at our Mobility Administration Consumer’s Information. We profile the very best suppliers in the mobility management subject, record their important capabilities, and Observe our Base Line for each.
Bottom Line Mobile devices are now being increasingly employed on organization networks to access organization applications that include essential business enterprise data. To safeguard against security breaches via mobile devices, mobile security solutions have to page be an integral Element of any business’s All round cybersecurity tactic.
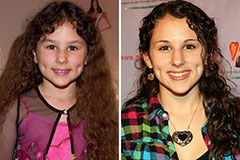 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Judge Reinhold Then & Now!
Judge Reinhold Then & Now! Andrea Barber Then & Now!
Andrea Barber Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now! Erika Eleniak Then & Now!
Erika Eleniak Then & Now!